Today, hardware manufacturers offer several security protections for the running Operating Systems (OS), such as Unified Extensible Firmware Interface(UEFI), Secure Boot, and Trusted Platform Module(TPM). These hardware technologies are designed to protect the underlying system being booted and are not necessarily designed to protect VM guests running in a virtualized environment.
Microsoft has invested in several areas leveraging UEFI, Secure Boot, and TPM technologies.
- Windows 11 – requires UEFI, Secure Boot, and TPM technologies.
- Microsoft Credential Guard requires UEFI, Secure Boot, and optionally will leverage the TPM technologies in protecting the key used by Microsoft Virtual Base Security.
- Microsoft Bitlocker optionally will leverage the TPM technologies to protect its keys to encrypt all the user and system files on the Windows drive.
- The Linux community can optionally leverage UEFI and Secure Boot.
This article will show how we can use these same technologies in a virtualized world, especially with Microsoft’s latest release of Windows, which requires UEFI, Secure Boot, and TPM.
Microsoft Windows 11 documentation outlines these requirements and provides detailed information on leveraging these capabilities. Be aware that Microsoft Windows documentation does not distinguish between running on a bare machine and running Windows in a hypervisor environment. Windows guest OS is unaware of the underlying hypervisor’s virtual implementation of UEFI, Secure Boot, and TPM. These features are implemented in the hypervisor, which is not required on the hardware.
In a virtual environment, a hypervisor such as AHV or ESXi allows multiple guests to run on a single hardware device sharing the hardware resources for the running guests. Hardware security technologies, such as UEFI, Secure Boot, and TPM, offer security protection between the hardware and the running hypervisor but do not provide direct benefit to the VM running within the hypervisor. Each hypervisor vendor has implemented a hypervisor software version extending the security benefits to the VM Guest. Let’s look closer at each of these technologies in a virtual environment.
Trusted Platform Module (TPM) Technology in the Virtual Environment
The Trusted Computing Group developed the specification for the TPM technology. TPM technologies are designed to provide enhanced Security and privacy in handling encryption operations. The purpose of the TPM is to ensure information storage is better protected from unauthorized access. The primary use case is storing secrets, making it difficult to access them without proper authorization.
The Trusted Computing Group outlines the TPM as a dedicated hardware chip that is soldered onto the motherboard in the computer, which works great in a bare metal deployment. In a virtualized environment using a hypervisor such as AHV or ESXi, the physical TPM chip approach does not scale to support multiple guest OS running on a single hardware configuration due to the following limitations.
- Key Storage – The storage available in a physical TPM chip can hold roughly three transient keys.
- TPM Isolation – The TPM chip does not provide any separation or isolation between multiple guest OS running on the same physical device.
To address the scaling issues for a virtualized environment, the hypervisor vendors have implemented a hypervisor-level software called virtual TPM (vTPM), which conforms to the Trusted Computing Group’s TPM specification. vTPM emulates these TPM specifications in the same functional manner as a physical TPM chip creating a private TPM instance per VM guest within the hypervisor. vTPM allows each VM guest to have its own key storage, isolating it from the other guests running on the same physical server. To maintain this isolation, the vTPM does not use the hardware physical TPM chip on the server.
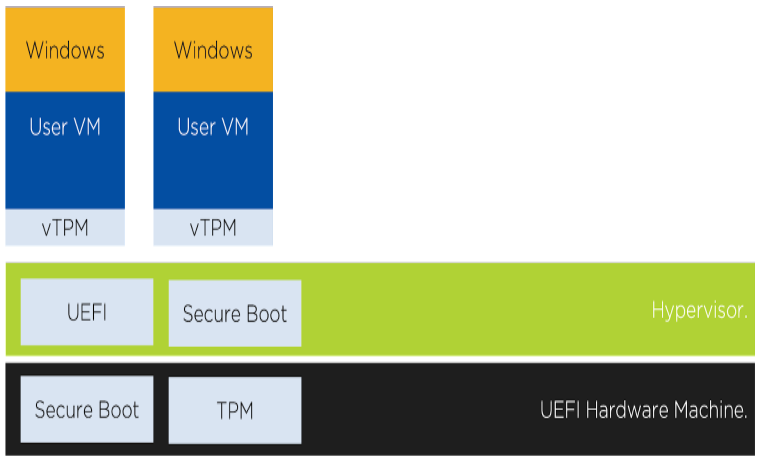
Each hypervisor vendor is responsible for protecting the vTPM instance from outside access. Nutanix AHV, for example, ensures isolation between VMs and encrypts vTPM data using a secure distributed secrets service called Mantle, preventing unauthorized access or tampering.
Unified Extensible Firmware Interface (UEFI)
UEFI is an open specification defining software interfaces between an operating system and the hardware or hypervisor platform. The UEFI organization describes the specification for UEFI.
UEFI is required to leverage advanced security capabilities such as Secure Boot. UEFI effectively replaces traditional BIOS implemented in most hardware and hypervisor platforms such as AHV and ESXi, booting guest OS such as Windows.
In a virtualized environment, hardware UEFI is used to boot the hypervisor. A hypervisor software implementation is used to boot VM guests under the virtualized version of UEFI, conforming to the UEFI organization specifications.
Hypervisor UEFI implementations such as those in AHV or ESXi do not require UEFI to be enabled on the hardware.
Secure Boot
Secure Boot is a feature within UEFI, and the UEFI organization defines these specifications. Secure Boot is designed to ensure what is being booted is trusted and that the boot binaries have not been tampered with. This helps prevent unauthorized software, like malware, from taking control of your system. This is accomplished by signature validation during the boot process. Its manufacturer will sign the operating system being booted, and UEFI will only allow trusted signatures before the boot process continues.
When the hardware boots the hypervisor, hardware UEFI will ensure that the underlying hypervisor binaries are safe and have not been tampered with. In a virtualized environment, the hardware Secure Boot feature will verify the hypervisor’s manufacturer signature before allowing the boot process to continue for the hypervisor.
Once the hypervisor is running, the hypervisor’s implementation of UEFI will handle the Secure Boot validation for VM guests during VM boot. Guest VM Secure Boot does not require Secure Boot to be enabled on physical hardware.
The Nutanix AHV virtual implementation of UEFI, Secure Boot, and vTPM allows you to run a more secure guest VM on top of the Nutanix security-focused infrastructure layer, including the latest version of Windows OS which requires these features to be enabled.

